How Hackers Kick Victims Off of Wireless Networks
Hello, my fellow pirates! Today we will cover a little penetration of Wi-Fi networks. Specifically, we will learn how to expel other people from wireless networks, even when we are not connected to them ourselves! We will use an external wireless adapter for this, so if you do not have an adapter, I strongly recommend getting one device, as it is an essential part of the Wi-Fi hacking equipment! The wireless adapter I will use in this lesson is the Atheros Ar9271, which can inject packets (injections are a very important feature for our wireless adapter). Now that we are out of this way, let's start!
Step 1: Configure the Wireless Adapter for the Attack
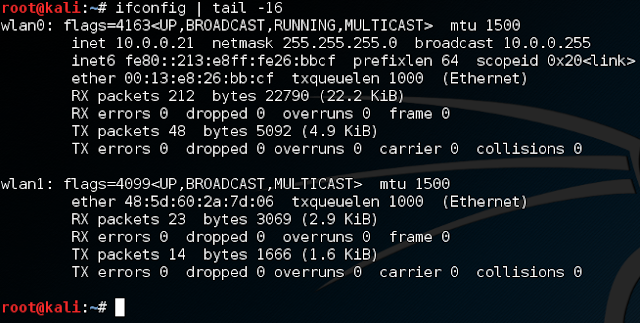
If we use our wireless adapter for this attack, we will need to configure it to do so! First, let's get an overview of our current wireless adapter setup:
Now, for this demonstration attack, we will connect the embedded wireless card (wlan0) to the target network. Then, we will use our external wireless adapter (wlan1) to lift ourselves off the network. After that, let's put our external adapter in screen mode:
First, we use ifconfig to set the interface down. After that, we use iwconfig to change it to the watch mode, then return it to its correct position. Now, when we check the iwconfig output shows that our external adapter is in screen mode. Now that our adapter is equipped for this attack, let's move on to it.
Step 2: Sniff for Target Networks
If we start from a wireless network, we'll need to select the network we use first! For this, we will use a tool called airodump-ng. This will allow us to view all wireless networks in our region:
Step 3: Sniff for Victims on the Target Network
Well, we have two networks around us. The network that our integrated adapter is running is NETGEAR89, so let's do some sniffing specifically for this network. From this information here, we will use BSSID and NETGEAR89 network channel number. So, let's re-execute airodump-ng and pass this information on:
Now, once this is done, we should be able to see information about customers connected to this wireless access point (WAP):
Well, after we have this information about the callers, we can move on to the next part of the attack. (Note: For the next part of the attack to work, we need to run airodump-ng, so leave this station open, and you've only minimized it.)
Step 4: Inject Deauthentication Frames into the Target Network
Now that we have the information about the target network, and the clients on the network listed, we can finally execute an attack cancel the authentication and turn off ourselves. The tool we will use to pump deauth frames into the grid is aireplay-ng. This is what we will use to start aireplay-ng:
Here we define deauth attack and say aireplay-ng for injection only once. Then we use the -a tag to give the BSSID to the target network. When you end the command, we assign the client to deauth using the -c tag followed by the MAC address of the victim. Now, let's do this and wait.
After completing the injection, we should be able to take a look at our wireless adapters and see that we are no longer connected to the wireless network:
There we have it. After our deauth attack, we can see that the internal (wireless) PCI adapter has been disconnected from the wireless network, we did it! This is just the beginning of Wi-Fi piracy here on HackingLoops. In the near future, we will try to build our own versions of the tools we have used here, so that we can develop a better understanding of how these tools work. When we build these tools, we will use Scapy and Python, so if you do not read our articles on these topics, I recommend it!






No comments